MFA-Phishing as Initial Access in Red Teaming
1. General Information
Phishing is one of the largest cyber threats frequently used as an initial access vector by criminal groups (see T1566 - Phishing, MITRE ATT&CK Framework).
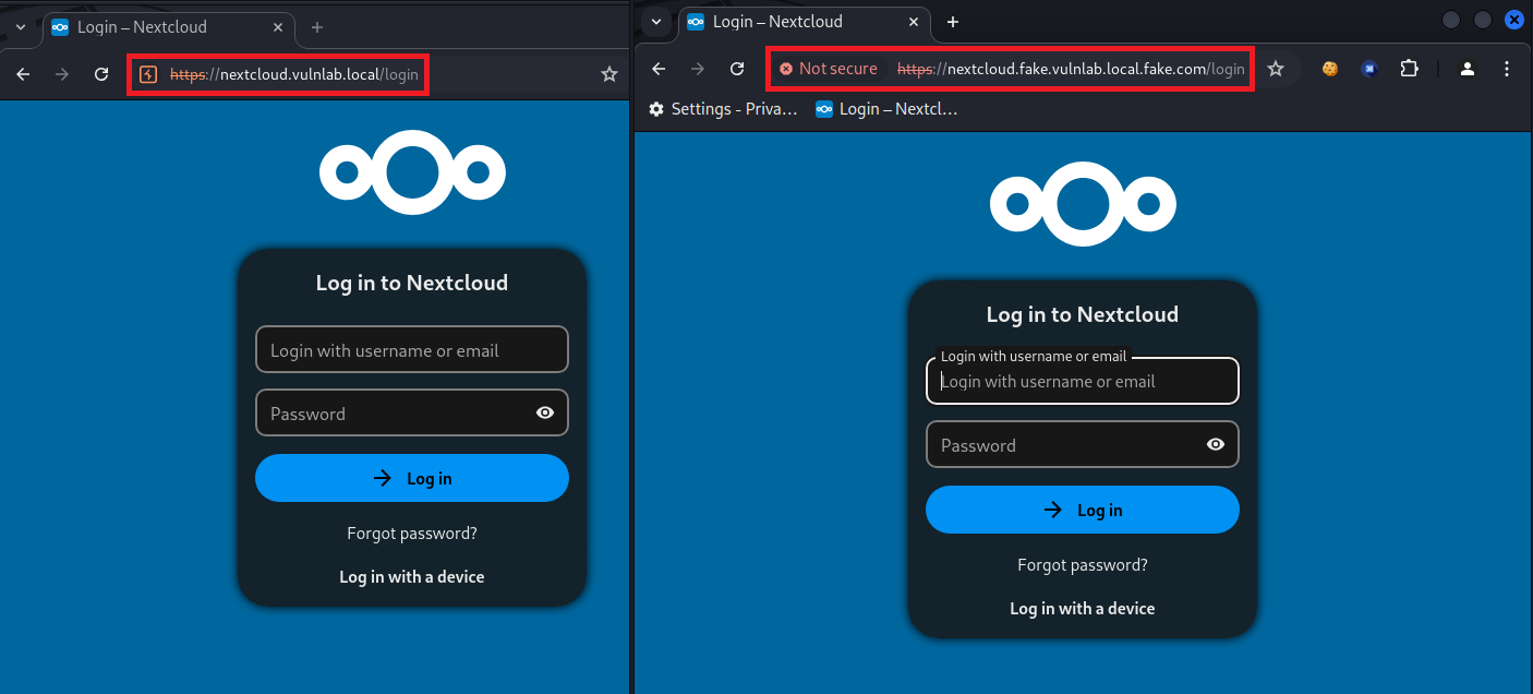
In classic phishing, an attacker creates a fake website that visually resembles a legitimate website. The attacker then sends an introduction text that is specifically tailored to phishing purposes and often applies pressure, along with a link to their malicious target page.
The victim is coerced by this pressure into visiting the fake website and entering their login credentials (username and password). An attacker can then use the intercepted login data to gain access to email accounts or perimeter systems (e.g., firewalls or VPN gateways). As a result, potential access to the affected person’s email account can lead to the espionage of personal data or trade secrets. This and other data could be offered for sale on the dark web to criminal actors. Common attack targets are users of cloud services, such as Microsoft 365 or social media platforms. In particular, access to cloud infrastructures intercepted by cybercriminals can serve as a potential gateway into the internal network.
As a protection against phishing attacks and password guessing (brute-force), Multi-Factor Authentication (MFA) has been developed, which has proven to be an effective safeguard. It requires, in addition to the standard login (using username and password), one or more verification factors to grant a person access to an online service. This makes it more difficult for an attacker to gain access to applications using stolen passwords since they still lack the additional factor.
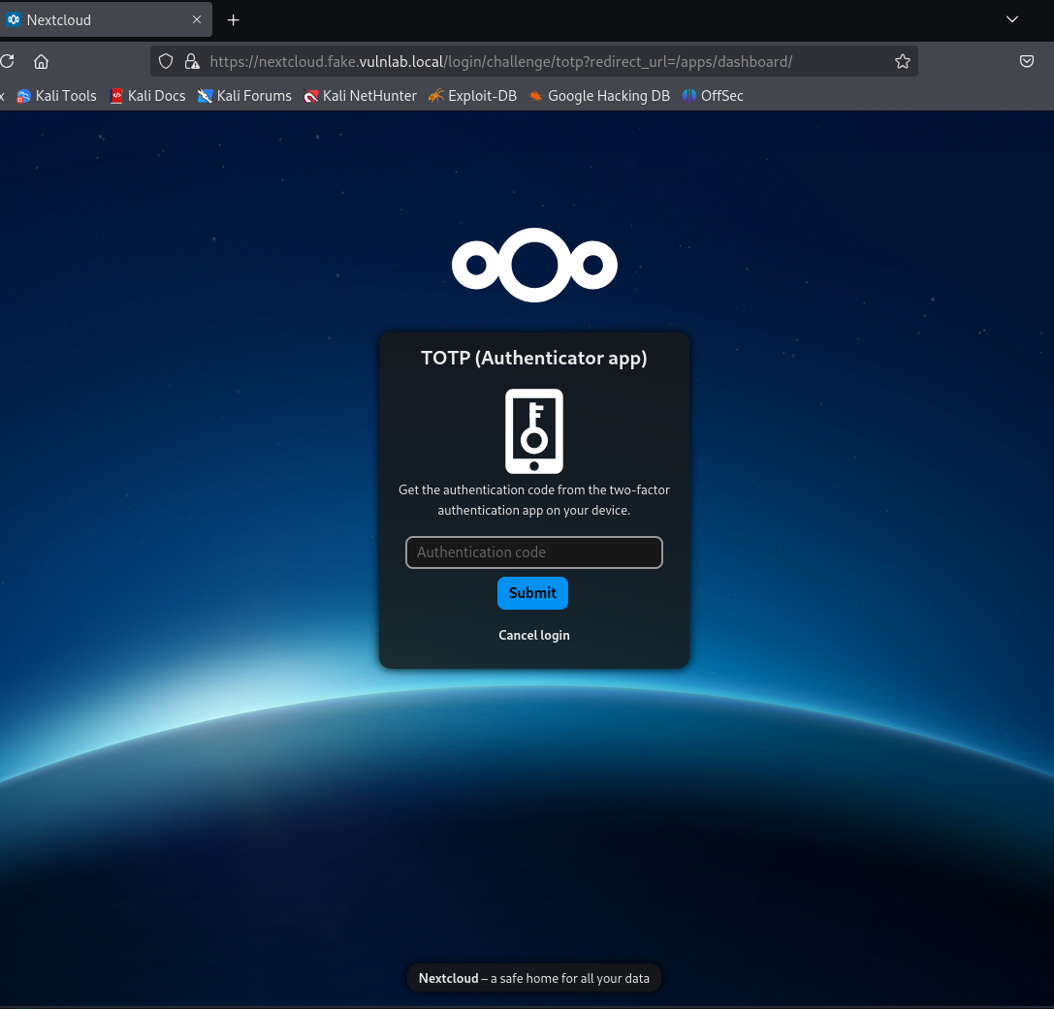
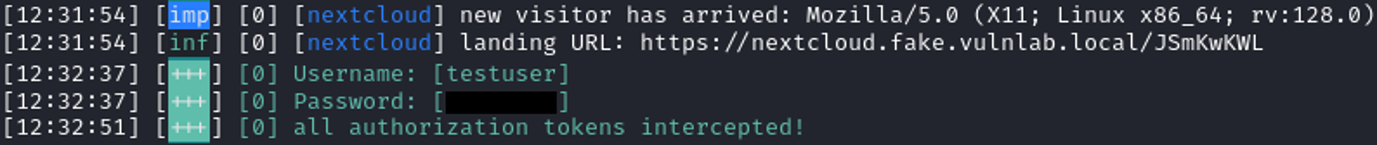
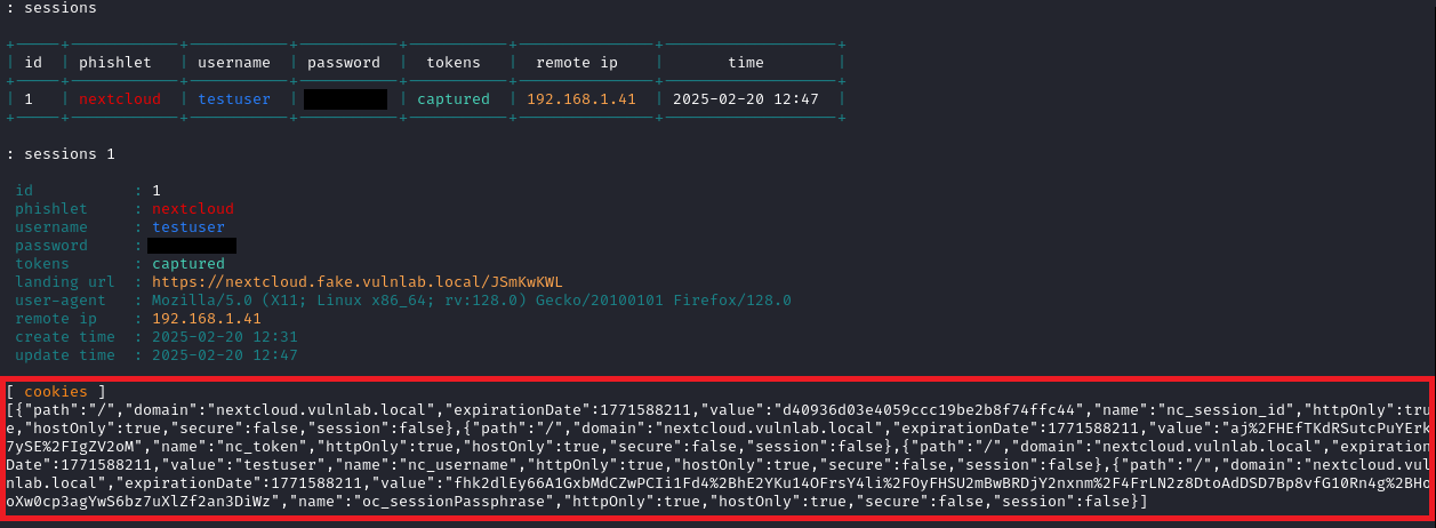
Attackers have developed so-called “MFA phishing” to circumvent Multi-Factor Authentication. The focus of this attack technique lies primarily on intercepting session cookies that are issued after a successful login. Unlike classic session hijacking, the attacker can easily read the username and password, and furthermore, multiple session cookies can be extracted.
To carry out MFA phishing, cybercriminals use well-known open-source frameworks such as Evilginx or Modlishka.
Classic phishing, where a user clicks on a link in a phishing email and is redirected to a specifically crafted page, has been enhanced with a Man-in-the-Middle (MitM) technique. The affected person first connects to a transparent proxy server (a web server between a person and the target website), where the attacker eavesdrops on the communication.
As a result, cybercriminals can intercept sensitive information through the proxy server, as all inputs (e.g., username or password) initially arrive at the proxy server in encrypted form using a TLS certificate. However, since the encrypted communication channel is established between the person and the proxy server, all transmitted data can be decrypted by the proxy, which knows the TLS certificate. Subsequently, the data is re-encrypted before being forwarded to the actual target page.
The following figure illustrates the functionality of the transparent proxy server (Evilginx).