Compromises to your own IT infrastructure are not always so obvious that they are detected immediately – for example, through a sudden system failure or a blackmail message appearing on the screen. Only 10% of all attacks are detected within the first hour, and less than 20% within the first few days. More often than not, cyber criminals have been in the network for weeks or even months, leaving only subtle, hard-to-detect traces. These symptoms can be so inconspicuous that they get lost in the mass of systems and processes of a large IT infrastructure. Often, there is only a vague feeling that ‘something is wrong’ without being able to identify the source of the problem. Sometimes suspicious behaviour is only noticed by third parties, such as service providers or the police. When company data turns up after seizures, for example, the surprise is often great and a key question arises: How could the data have been lost?
The threat hunting approach could offer a solution to this problem. Threat hunting is a proactive approach to searching for hidden and unknown threats in networks and systems. This is usually done on the assumption that criminal actors have already infiltrated the company network, even if no obvious symptoms have yet appeared.
Companies with an integrated Security Operations Center (SOC) as part of their security strategy usually let the SOC take care of threat hunting. A SOC is responsible for central monitoring, assessment and defence against cyber threats. But what if a company does not have a SOC and still needs to quickly check multiple IT systems due to an unknown threat? In this case, an infrastructure must be provided as quickly as possible to take on this task.
Such a scenario requires an easy-to-set-up and flexible infrastructure that enables analysts to quickly gain an overview of the system landscape and search for threats on relevant systems within a network.
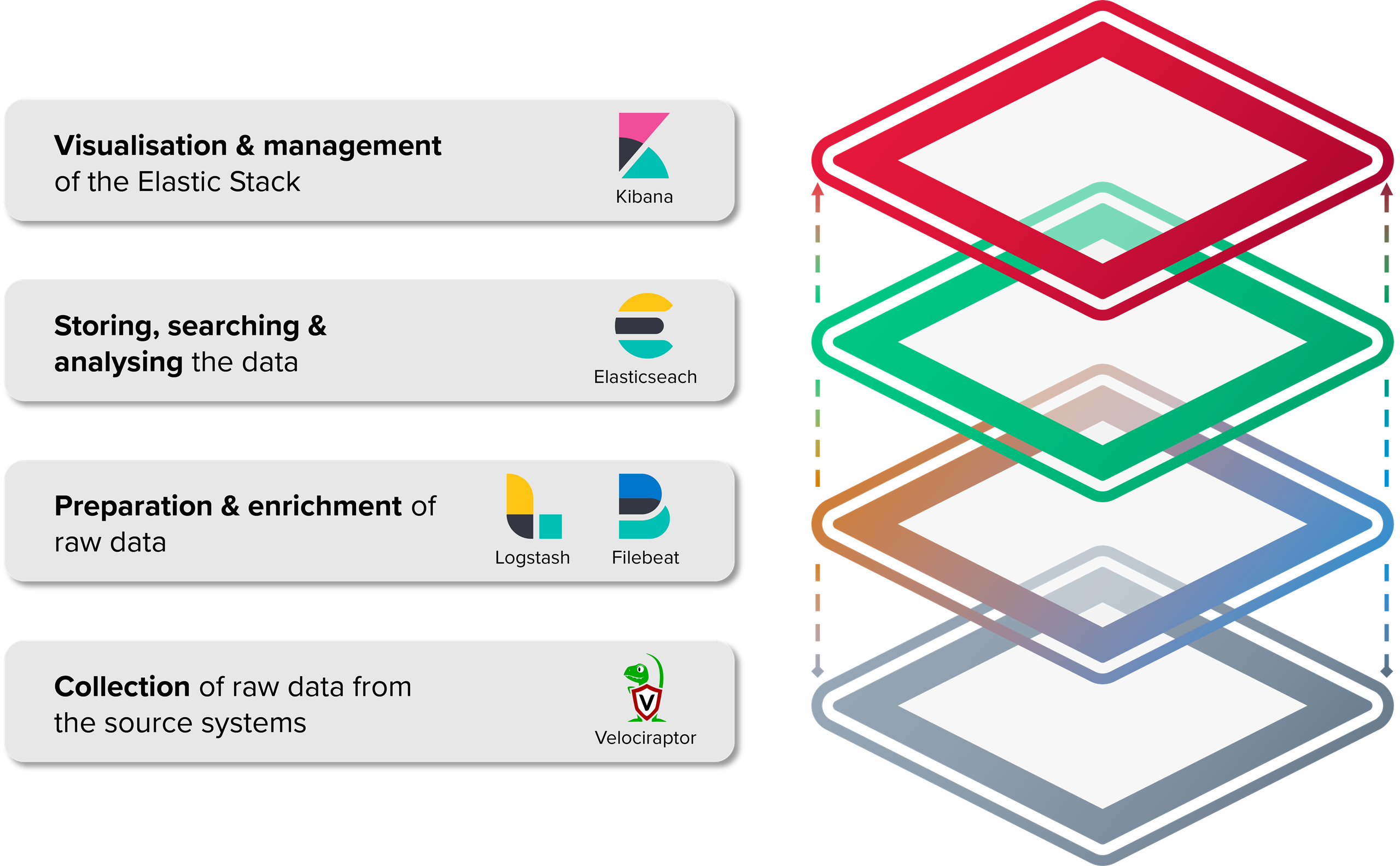
This is where VELK comes in - a solution that essentially consists of two central components:
- Velociraptor - a platform for incident response and IT forensic activities
- The Elastic (formerly ELK) stack - a platform for data collection, processing and visualisation.
The aspect of an easily scalable and flexible infrastructure is realised through the use of the following solutions:
- Docker - to create an isolated environment that can be created and cleaned up quickly
- Cloud hosting (e.g. Azure) - for rapid deployment, scaling and connection to the infrastructure to be monitored
The core idea behind the combination of Velociraptor and the Elastic Stack lies in the effective triage, the collection of IT forensically relevant information (so-called artefacts) from end devices, as well as their central consolidation and processing. This combination enables a scalable and visual solution that can be flexibly expanded and adapted to case-specific investigation objectives.
Velociraptor takes over the collection of forensic data from the endpoints. The collection itself can be specifically adapted to the relevant scenario and customer environment via Velociraptor by adding or omitting artefacts, e.g. depending on the operating systems used. The collected data is then stored in a storage to enable further processing in the Elastic Stack.
The Elastic Stack consists of the following three main components:
- Elasticsearch - a NoSQL database for storing and indexing the processed data
- Logstash - handles the processing, transformation and enrichment of the data
- Kibana - is used to visualise and analyse the data
Elastic Beats are also important for processing within the pipeline. Filebeat collects the data from the storage and sends it to Logstash via the Beats API. Logstash processes and transforms the received data, enriches it with additional information such as geodata ("enrichment") and stores it in an Elasticsearch database (a so-called index). Corresponding configuration files are used for this. For reasons of compatibility, the Elastic Common Schema (ECS) is used for the transformation process, where appropriate. By using the ECS, a normalisation is carried out in which the data is converted into a uniform format in order to create a consistent, comparable and easier to evaluate database.
Once the data has been transformed using the Logstash component and stored in Elasticsearch, the transformed and enriched data can be retrieved, visually processed and analysed using the Kibana component.
Monitoring solutions such as Metricbeat and Grafana are used to monitor the functionality of the entire pipeline. These tools help to continuously monitor the functionality of the infrastructure and ensure that all components are working efficiently and stably.
Conclusion
Thanks to a flexible infrastructure, the VELK solution enables a fast, targeted and effective response to suspicious behaviour and subtle attacks, which can then be investigated. Attack vectors and propagation can thus be recognised and an understanding of the threat and containment developed. Thanks to the ad-hoc solution and a high degree of automation as well as intelligent enrichments, our incident response experts can pursue threat hunting to clarify issues such as data outflow despite a lack of preparation. However, the integration of a high-performance Security Operations Center (SOC) in combination with an incident response service is recommended to strengthen cyber resilience in the long term.

